Recently I was having trouble connecting to a Data Protection Manager server from a remote machine using power-shell cmdlets. I knew I had everything properly configured with DPM, and so I knew it was probably Windows Firewall that was blocking access to the computer.
What I needed was a log of what was being blocked and here is how I was able to turn on logging on the machine (a Windows 2008 server).
Under “Administrative Tools” select “Windows Firewall with Advanced Security”
Click on the topmost node: “Windows Firewall with Advanced Security on Local Computer”
Select “Windows Firewall Properties”
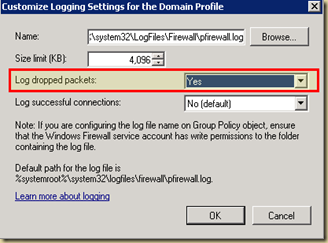
In my case I needed logging turned on for my Domain profile, so on the Domain profile tab, I clicked on the Customize button in the logging section and turn on logging of dropped packets:

The log file is by default created at: “%systemroot%\system32\LogFiles\Firewall\pfirewall.log”
If you look at the log file you will find out the protocol that the remote machine is using to connect and the port. Depending on your specific situation you will have to add an incoming rule (or outgoing rule) to allow the appropriate connections through.



No comments:
Post a Comment